Коррозия на дисках автомобилей - это распространенная проблема, особенно в областях с агрессивными климатическими
Процесс сертификации предполагает тщательное тестирование и проверку продукции с целью убедиться в ее соответствии
Пожарная сертификация является ключевым процессом, обеспечивающим безопасность продукции и сооружений в случае пожара.
Седан OMODA S5 относится к популярному Golf-классу (С-классу) и является второй моделью нового автомобильного бренда после
Технические регламенты Таможенного союза оказывают значительное влияние как на производителей, так и на потребителей.
Автомобильная промышленность Азии, особенно Японии, Кореи и Китая, за последние десятилетия продемонстрировала значительный рост
Мотоциклы с аукционов Японии представляют собой отличный способ приобрести качественный транспорт по разумной цене.
Хранение шин является важной задачей для любого автовладельца, поскольку от правильности хранения зависит срок
Покупка автомобилей с аукционов Японии с доставкой https://estransit.ru/ возможна и пользуется популярностью у многих покупателей
Покупка автомобилей без пробега по РФ может быть выгодной для тех, кто ищет свежие
Перед приобретением автомобиля с аукциона Японии рекомендуется провести собственное исследование и обратиться к надежному
Покупка японских автомобилей через аукцион - это один из самых популярных способов приобретения автомобилей
Таможенное оформление автомобилей – это процесс, который требуется для регистрации автомобиля, купленного за границей, и
Acura RDX 2009 года - это компактный кроссовер, который был представлен компанией Honda под
Для того, чтобы обеспечить длительный срок эксплуатации этого автомобиля, следует придерживаться рекомендаций по техническому
Зимние шины - это тип автомобильных шин, который специально разработан для лучшего сцепления с
Существует еще и промежуточный вариант, это так называемые всесезонные шины. Они мягче обычной летней
Популярностью аренда машины без водителя пользуется у тех, кто стоит перед вопросом выбора авто
Статистика показывает, что около трети автомобилистов не могут оплатить полную сумму по разным причинам.
Тела умерших ранее перевозили на специальных колесницах или телегах, а с начала 20 века
При выборе арматуры, которая может использоваться для различных целей, нужно обязательно учитывать ее технические
Катушка зажигания Если загорелся чек на панели Kalina, автовладелец проверил свечи и с ними
Лада Калина заглохла на ходу и не заводится, стартер крутит, что делать Лада Калина
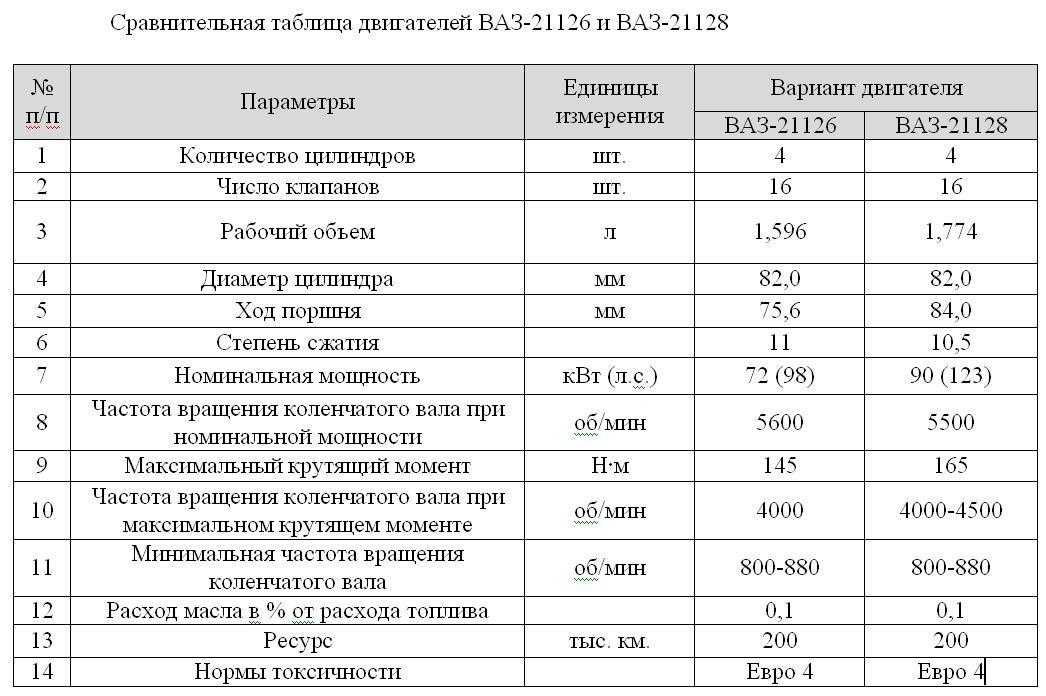
Разгон с 0 до 100 км/ч, холодный запуск, конструктивные особенности двигателя ВАЗ 11193. Что
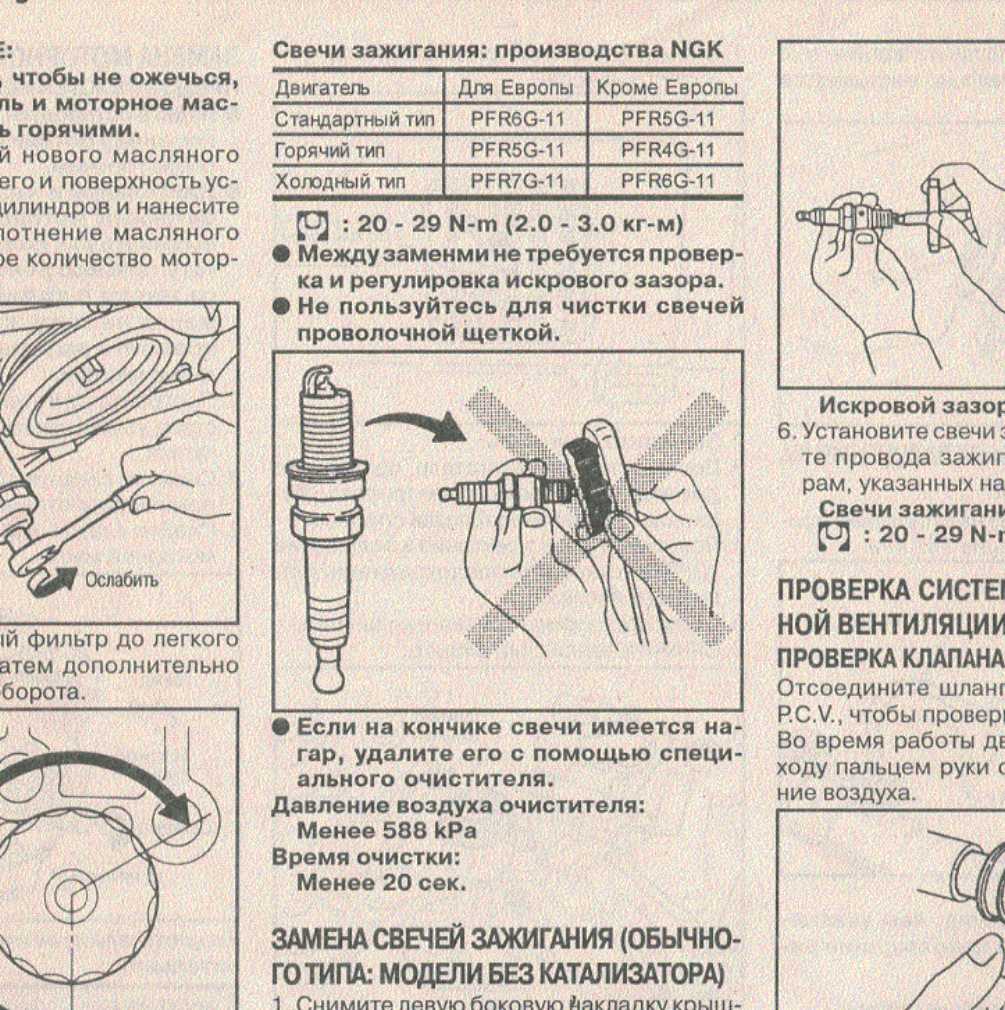
Зазор на свечах зажигания, почему важно чтобы был выставлен правильный зазор и каким образом
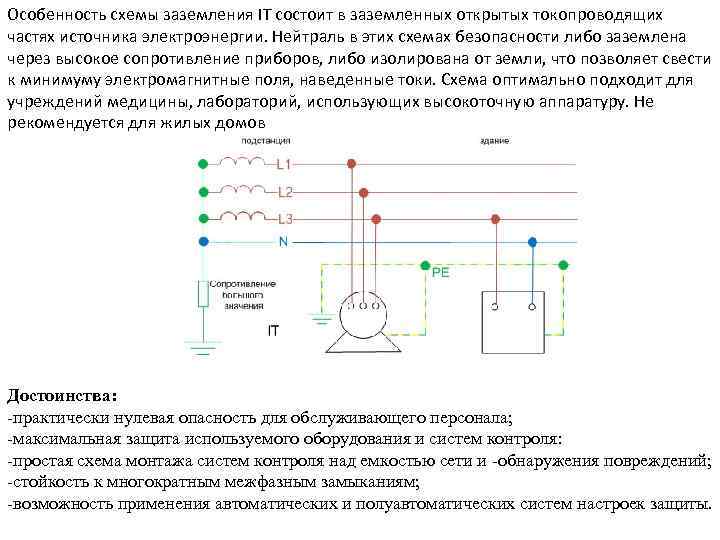
Правила устройства электроустановок (ПУЭ) 7-е издание. ПУЭ-7 п.1.7.100-1.7.126
Устройство мотоблока «ОКА».Рекомендации по обкатке, настройке, обслуживанию и эксплуатации.Основные неисправности двигателя.Установка и замена ремней.Свет
Вопрос знатокам: Как водить машину .Сталкер тень чернобыля.... За ранее спасибо: -))))))))) С уважением,
Почему не заводится машина с сигнализацией Пантера и не работает автозапуск на автомобиле? Причин